Are you ready to unlock the full potential of your IoT devices from anywhere in the world? The convergence of Virtual Private Cloud (VPC) technology, Secure Shell (SSH), and the compact power of a Raspberry Pi offers a gateway to remote IoT management like never before.
The Internet of Things (IoT) is rapidly reshaping industries, connecting devices in unprecedented ways. The ability to manage these devices remotely, securely, and efficiently is now a necessity, not a luxury. This article delves into the critical components of setting up RemoteIoT with VPC, SSH, and a Raspberry Pi, providing a comprehensive guide for both beginners and seasoned developers. As we move forward in this journey, you'll gain a deeper understanding of how to build a secure and efficient remote IoT environment, armed with the right tools, practices, and expertise.
Table of Contents
- Introduction to RemoteIoT
- Understanding VPC Architecture
- Raspberry Pi Overview
- SSH Basics for IoT
- Setting Up RemoteIoT VPC
- Configuring SSH on Raspberry Pi
- Downloading RemoteIoT VPC Components
- Security Best Practices
- Troubleshooting Tips
Introduction to RemoteIoT
RemoteIoT signifies the capability to oversee, observe, and interact with IoT devices from a distant locale. This concept has surged in popularity due to its flexibility and scalability. By utilizing cloud computing and secure communication protocols, RemoteIoT empowers businesses and individuals to exert control over devices without requiring a physical presence.
- Paris Hiltons Motherhood Journey Baby Head Moments More
- Nischelle Turners Husband What You Should Know Updated
Why Embrace RemoteIoT?
The preference for RemoteIoT in IoT management stems from several key advantages:
- Enhanced efficiency in device management.
- Reduced operational costs through the minimization of on-site visits.
- Fortified security via encrypted connections.
- Scalability to accommodate expanding IoT networks.
VPC Architecture
A Virtual Private Cloud (VPC) is a dedicated network environment within a cloud platform. It allows users to create isolated environments for their applications and services, ensuring security and performance. When combined with RemoteIoT, VPC provides a robust framework for managing IoT devices.
Key Features of VPC
VPC offers several features that make it ideal for RemoteIoT setups:
- Jonathan Rhys Meyers From The Tudors To Resilience Amp Beyond
- Henry Chos Wife A Look At Jill Chos Life Partnership
- Private subnets for secure communication.
- Internet gateways for external access.
- Network Access Control Lists (NACLs) for fine-grained control.
- Integration with cloud services like AWS or Azure.
Raspberry Pi Overview
The Raspberry Pi is a compact, affordable single-board computer widely used in IoT projects. Its versatility and ease of use make it an excellent choice for implementing RemoteIoT solutions. With support for various operating systems and programming languages, the Raspberry Pi can be customized to meet specific project requirements.
Advantages of Using Raspberry Pi
Here are some benefits of using Raspberry Pi in RemoteIoT setups:
- Cost-effective hardware solution.
- Extensive community support and resources.
- Compatibility with numerous sensors and peripherals.
- Low power consumption for long-term deployments.
SSH Basics for IoT
Secure Shell (SSH) is a cryptographic protocol used to secure network communications. In the context of RemoteIoT, SSH ensures that data transmitted between devices and the cloud is encrypted and protected from unauthorized access. Understanding SSH basics is crucial for setting up a secure IoT environment.
How SSH Works
SSH operates by establishing an encrypted connection between a client and a server. The process involves:
- Authentication using passwords or public key cryptography.
- Data encryption to prevent eavesdropping.
- Integrity checks to ensure data has not been tampered with.
RemoteIoT VPC Setup
The establishment of a VPC for RemoteIoT involves several crucial steps, including the creation of subnets, the configuration of security groups, and the deployment of instances. Below is a detailed, step-by-step guide to help you begin this process:
Step 1
Initiate the creation of a new VPC using your preferred cloud provider's console. Specify the desired IP address range and other essential network settings to tailor the VPC to your specific needs.
Step 2
Segment your VPC into distinct subnets, including both private and public subnets. This separation is essential for achieving proper network segmentation, which enhances both security and organizational structure.
Step 3
Configure security groups to precisely control the flow of inbound and outbound traffic to your instances. These groups act as virtual firewalls, allowing you to define specific rules based on your traffic requirements.
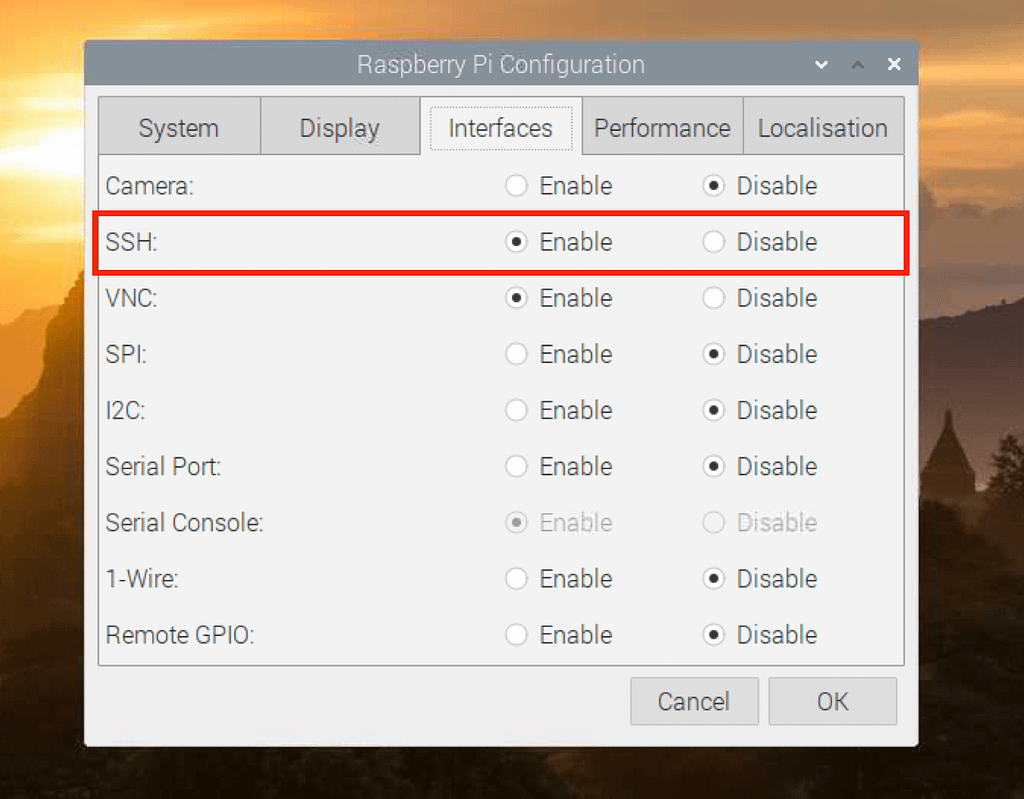
Raspberry Pi SSH Configuration
Configuring SSH on a Raspberry Pi is a relatively straightforward process. Follow these steps to enable SSH and establish a secure connection:
Enabling SSH
To enable SSH on your Raspberry Pi, you have two primary methods:
- Utilize the Raspberry Pi Configuration tool, which provides a graphical interface for easy setup.
- Create an empty file, named "ssh," on the boot partition of your SD card. This file signals the system to enable SSH during boot.
Securing SSH
Once SSH is enabled, it is crucial to implement several security measures to protect your connection:
- Modify the default SSH port, opting for a non-standard value to reduce the risk of automated attacks.
- Deactivate password authentication and, instead, implement public key authentication. This method significantly enhances security by using cryptographic keys.
- Restrict SSH access to specific IP addresses using firewall rules. This limits the potential attack surface and enhances network security.
Downloading RemoteIoT VPC Components
Downloading the necessary components for your RemoteIoT VPC setup involves accessing the appropriate software repositories and installation packages. Here's how you can proceed:
Step 1
Determine which software and libraries are needed for your project. Common components include:
- SSH server software (e.g., OpenSSH).
- Cloud provider SDKs (e.g., AWS SDK, Azure SDK).
- IoT device drivers and libraries for interacting with sensors and other peripherals.
Step 2
Download the required components from official repositories or trusted third-party sources. Always verify the integrity of the downloaded files to ensure security. Use checksums (like SHA-256) to validate that the downloaded files have not been tampered with.
Security Best Practices
Security is paramount when dealing with RemoteIoT setups. Follow these best practices to protect your devices and data:
Regular Updates
Maintain the security of your operating system and applications by promptly updating them to patch any known vulnerabilities. This includes applying security patches and updates released by the software vendors.
Network Segmentation
Employ VPCs and subnets to isolate your IoT devices from other network resources. This compartmentalization helps to limit the impact of a security breach, containing any potential threats.
Monitoring and Logging
Implement robust monitoring tools to vigilantly detect and promptly respond to any suspicious activities. Regularly review logs to identify anomalies and take appropriate action. Utilize intrusion detection and prevention systems (IDS/IPS) to further enhance security.
Troubleshooting Tips
Encountering issues during your RemoteIoT VPC SSH Raspberry Pi setup is common. Here are some troubleshooting tips:
Check Network Configuration
Carefully examine your network settings to ensure that they are correctly configured. This includes verifying IP addresses, subnets, and the configuration of security groups. Ensure that firewall rules allow the necessary traffic.
Verify SSH Settings
Thoroughly double-check your SSH configuration files for errors or misconfigurations. Examine the `sshd_config` file for settings related to port, authentication methods, and access restrictions.
Consult Documentation
Refer to the official documentation provided by your cloud provider, Raspberry Pi, and SSH software. Explore community forums and online resources for guidance on resolving specific issues that you may encounter.
- Erin Kellyman Biography Career Future Projects A Rising Star
- Amanda Tapping From Stargate Sg1 To Directing Beyond